The Cyber Crimes are increasing day by day, the people who do such things try to leave no forensic evidence. Sometimes the criminals make use of the Internet which makes tracking the users of a Web page complex and difficult to collect the evidence of digital crimes includes network traffic, network devices, storage devices, mobile devices etc. The Browser history, registry entries and cookies on the client side and the log files on the server side are some of the potential sources where one can track the user’s actions and find evidence of occurrence of a particular event. In this respect we try to focuses on the forensic analysis of Web Browsers like Internet Explorer, Safari, Google Chrome, Mozilla Firefox, etc. Now a day’s Internet is essential application for everyday work and Web browsers are used as a main tool to connect the internet world. Users are generally use web browser for e-mail access, social networking sites, internet banking, news, entertainment, update related information’s, e-commerce and searching relevant information’s. Where the common user use internet for own work and attackers use it to get advantages of user’s limited knowledge and perform many Cyber-attacks. A suspect uses the internet to hide the crime, or to search idea of new crime space. Every time when suspect perform any unethical activity using the browser, he /she try to remove their activity details. So collecting the evidences from web browser for the evidence purpose is typically crucial activity. Even there is many open source browser forensics tools are available. But problem is that every tool has limitation like non-supportability of browser, non-supportability of browser version, on-supportability due to frequently update the browsers, etc.
History of Browsers
Current day browsers are based on the idea proposed by Tim Berners-Lee and Robert Cailliau back in 1990 the WorldWideWeb (not to be confused with the World Wide Web) was the first browser ever created by W3C Director Tim Berners-Lee, mainly to create a medium to distribute research papers to other interested people, then renamed Nexus to differentiate from the actual World Wide Web. Unlike today, this was the only browser and the only way to access the web. This led them to create the first browser known as the WWW short for World Wide Web . In 1992 introduced Lynx was a texted-based browser that couldn’t display any graphic content. In 1993 came Mosaic, a browser that could display text and images together, designed for use by anyone—not just the highly technical and/or academic crowd the Internet catered to prior to this point. Mosaic was created by the University of Illinois’ National Center for Supercomputing Applications and was embraced by users across the globe. Built by many of the same people that created Mosaic, Netscape Navigator came onto the scene in 1994. Included in this browser’s many advancements was its design for the speed of dial-up modems common in private households. Early Internet adopters often used the phrase “Best if viewed in Netscape” on their websites, and many of us followed suit. Also in 1994 came Opera, which is particularly impressive since this is a browser still going strong today (a rare longevity in the web world). In 1995 came Internet Explorer made its debut as Microsoft’s first web browser. While Internet Explorer (IE) had earlier versions, such as the original that launched fully integrated with Windows 95 operating systems, it was IE 3, which arrived in 1996, that started a shift in browser dominance. It supported multimedia applications and Internet mail among many new features. With the weight of Microsoft behind it, Internet Explorer quickly became a force, becoming the leading browser by 1999. In 1996 Opera started as a research project in 1994 that finally went public two years later. This was also arguably the beginning of the browser wars, mainly between IE 3 and Navigator 3 as Internet Explorer inched ahead with new capabilities. Steve Jobs introduced Apple’s first web browser, Safari, in 2003, which became included specifically for Macintosh computers operating systems. IE in many ways killed Netscape, but it found a major competitor with the launch of Firefox in 2004. Built by Netscape Navigator spin-off, Mozilla, Firefox started changing the landscape of web browsers into the competitive space we now know today. Open-source at its core, Firefox was an answer to both those who found Internet Explorer imperfect and those who feared its level of privacy. In 2007 Mobile Safari was introduced as Apple’s mobile web browser and continues to dominate the iOS market. In 2008 Google Chrome appeared to soon take over the browser market, Google Chrome web browser which came as a surprise by a company whose main business is internet search engine. It mainly happened after they hired a group of developers from Firefox and demonstrated a working model of Chrome. The code for the browser was kept as open source. This helped other developers, learn the code and help in porting into other operating systems such as Mac OS and Linux based systems. As of today Google Chrome is the third most widely used browser followed In 2011 Opera Mini was released to focus on the fast-growing mobile browser market. In 2015 Microsoft Edge was born to combat Google.
This was the time browser developments turned into a war between the companies to increase their market presence. The companies kept releasing on a monthly basis a new versions of the browser without thinking about fixing bugs from earlier releases. This also made them only think about thrilling the clients with rich features and not follow standard coding practices released by W3C. This made the companies only think about adding new features and not worry about security. Therefore, the browsers released during that period were poorly designed in terms of code. Due to this each release handled the tags and display layout differently and also had compatibility issues on different platforms (As Microsoft and Macintosh etc.).
Main Features Of Web Browser Forensics
Every forensic investigation should follow proper set of process and procedures for the evidence to be admissible in the court of law. The process used to retrieve the evidence till getting the final results should be repeatable using the process and procedure. During an investigation the below are the different kinds of evidences that an investigator would be looking for:
a. Surfing history: Surfing history of a user would mainly contain typed URLs, redirects and also the number of visits to a particular site.
b. Bookmarks: This would mainly contain shortcuts or bookmarks created to specific websites by the user.
c. Downloads: An investigator would mainly need to check for downloaded file in the default locations, also in the user defined locations or sometimes files are downloaded to default locations and then are moved or copied to user defined locations.
d. Cookies: These are files that contain a wealth of information about the user. It would contain information like usernames, passwords and web session information.
e. Cache: It is a temporary area on the disk which is used to store most recently visited web sites.
As referenced earlier, forensics is mainly performed to collect evidence based on the subject of the case. The evidence can be collected from different parts of a communication channel. Those different parts can be: Server side which stores access logs, error logs, application logs, system logs etc; Intermediate site logs which can be from firewall logs, router logs, anti-virus logs, web filter logs, switch logs, network access control logs etc; Client side which stores temporary internet files, index.dat files, history.dat, cookies, favourites, html stored in unallocated space, registry etc. Our main topic of discussion is with regards to client side logs and mainly pertaining to web browser. To help an investigator, researchers have written papers clearly explaining where to look for evidence for different browsers installed on different operating systems. Below is a list of browsers and different techniques of extracting evidence from them.
I. Internet Explorer:
Windows XP: On Windows XP systems, IE stores data in the “drive:\Documents and Settings\<username>\ profile folder. Folders that you would find there would be Favourites, Cookies, History and Temporary Internet Files. Also Registry stored information like Typed URLs, Passwords and Protected Storage Information.
IE Temporary Internet Files are stored in drive:\Documents and Settings\<username>\Local Settings. This folder contains an index.dat file that stores URL, Filename, Username and Content Info. This also provides us information even if the user deletes their Temporary Internet files.
The Registry saves the Typed URL at NTUSER.DAT\Microsoft\Internet Explorer\Typed URLs. The Protected Storage System Provider stores user IDs and passwords for websites at NTUSER.DAT\Software\Microsoft\Protected Storage System Provider. This is usually stored in encrypted form which can be viewed in clear text using Registry Viewer, tool by Access Data.
Windows Vista/7/8/10: On Windows Vista and Windows 7 systems, the cache and history information is stored in drive:\Users\<user name>\AppData\Local\Microsoft\Windows\. The cache here would contain files stored from different webpages browsed by the user. The history would tell you what sites someone has visited, when and how many times.
The cookies, that can contain a password or a session ID to a website they had authenticated to, are stored in drive:\ Users\<user name>\AppData\Roaming\Microsoft\Windows\Cookies.
The Registry stores the Typed URL at HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TypedUrls, while the AutoComplete data like forms data and passwords at HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Intelli Forms. The form data and passwords are in obfuscated form and would need tools like Registry viewer or Pass View to view the data in clear text.
II. Firefox:
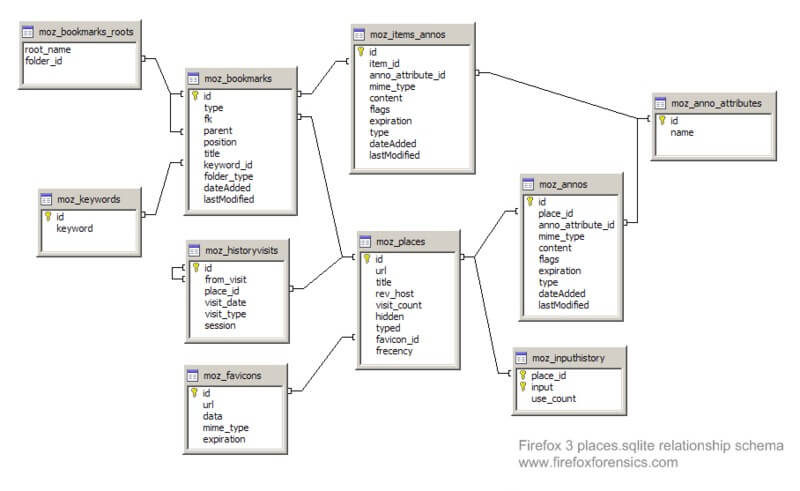
From version 3 onwards, Firefox stores all browsing information in a SQLite database instead of a flat file (mork file format). Below image shows the database structure used to store Firefox browsing information.
Web Browser Private Mode Forensics Analysis
The database files that are required are places.sqlite, formhistory.sqlite, downloads.sqlite, cookies.sqlite, search.sqlite and signons.sqlite.
a) places.sqlite
The places.sqlite database mainly consists of accessed URLs and bookmarks. Lot of tables stores this information, but the most important ones are:
Moz_places table is the central table where all the URLs are stored. The following fields are part of the moz_places table:
- id: This is the table’s primary key
- url: This stores URLs accessed
- title: this stores the title of the page
- visit_count: this stores the number visits count
- hidden: this is mainly used for URL queries and RSS feeds. This tells us if the URL would be displayed by the autocomplete functions. If the value is set to 1 would mean that it is hidden.
- typed: this would tell you if the URL was typed or not. A value of 1 would mean that the URL was typed and 0 would mean it was not typed.
- frecency: this is a score given to URLs, bookmarks, history and tags. The scoring is done based on the number of times the site was visited, the type of visit, last visit and if the URL was bookmarked or tagged.
The other important table within the places.sqlite database is the moz_bookmarks table. This stores the bookmarks and the following are the important fields:
- id: this is the tables primary key
- type: if the value is 1, it means that the entry is a URL. If the value is 2, it means it is a folder and 3 means a separator
- fk: a foreign key used to link the moz_places with the moz_bookmarks table.
- parent: this indicates parent folder id of this record, usually used in conjunction with position.
- position: this indicates the position of the record within the folder.
- title: the title of the page is stored here.
- folder_type: this identifier tells us if the record is a folder.
- dateAdded: this stores the time and date when the record was added.
- astModified: this stores the date and time when the record was last modified.
The moz_historyvisits is also another important table in the places.sqlite database. Below are the important fields:
- id: this is the table’s primary key
- place_id: this is a reference to the moz_places table
- from_visit: this stores the referrer information for the current page.
- visit_date: this stores the date and time the URL was accessed.
b) formhistory.sqlite
formhistory.sqlite database has just one table called moz_formhistory and this stores the id, fieldname and the value.
c) downloads.sqlite
again like formhistory.sqlite has only one table called the moz_downloads table and the important fields are as below:
- id: contains the tables primary key
- name: this stores the filename of the file being downloaded.
- source: source URL of the download
- target: directory where it was downloaded
- startTime and endTime: download start and end time.
- state: shows if the download is paused, completed or cancelled.
- referrer: stores URL information of the previous page.
- curnBytes: stores information about the current downloaded bytes
- maxBytes: stores information about the total bytes to be downloaded
d) cookies.sqlite
This file has one table called the moz_cookies and stores all of the cookie data like id, name, value, host, path, expiry, last Accessed, is Secure and is http Only.
Different operating systems store this information in different locations.
The different locations are:
Windows XP
C:\Documents and Settings\<username>\Application Data\Mozilla\Firefox\Profiles\<profilefolder>\
Windows Vista/Windows 7/8
C:\Users\<user>\AppData\Roaming\Mozilla\Firefox\Profiles\<profile folder>\
Linux based systems
/home/<user>/.mozilla/firefox/<profile folder>/places.sqlite
Mac OS X
/Users/<user>/Library/Application Support/Firefox/Profiles/default.lov/
/Users/<user>/Library/Caches/Firefox/Profiles/*.default/
/Users/<user>/Library/Caches/Firefox/Profiles/*.default/Cache/
There different tools developed by different people from the forensics community. The most popular tools are mainly Firefox 3 Extractor (also known as f3e) and FoxAnalysis.
III. Google Chrome:
Chrome also stores its history in SQLite database but the structure is different from Firefox. The History folder stores the database file that contains the browsing history and can be viewed using any SQLite browser. The important tables are downloads, presentation, urls, keyword_search_terms, segment_usage, visits, meta and segments. The most significant ones are downloads, urls and visits. The list of all downloaded files is stored in downloads table. The urls contains all accessed or visited URLs. And visits table contains the type of visit and the time the site was visited .
We can view the urls table by running the below query
sqlite> .schema urls
CREATE TABLE urls(id INTEGER PRIMARY KEY,url LONGVARCHAR,title LONGVARCHAR,visit_count INTEGER DEFAULT 0 NOT NULL, typed_count INTEGER DEFAULT 0 NOT NULL,last_visit_time INTEGER NOT NULL,hidden INTEGER DEFAULT 0 NOT NULL, favicon_id INTEGER DEFAULT 0 NOT NULL);
CREATE INDEX urls_favicon_id_INDEX ON urls (favicon_id);
CREATE INDEX urls_url_index ON urls (url);
The same can be done for visits table
sqlite> .schema visits
CREATE TABLE visits(id INTEGER PRIMARY KEY,url INTEGER NOT NULL,visit_time INTEGER NOT NULL,from_visit INTEGER,transition INTEGER DEFAULT 0 NOT NULL,segment_id INTEGER,is_indexed BOOLEAN);
CREATE INDEX visits_from_index ON visits (from_visit);
CREATE INDEX visits_time_index ON visits (visit_time);
CREATE INDEX visits_url_index ON visits (url);
Therefore user browsing information can be retrieved by running the query
SELECT urls.url, urls.title, urls.visit_count, urls.typed_count, urls.last_visit_time, urls.hidden, visits.visit_time, visits.from_visit, visits.transition FROM urls, visits WHERE urls.id = visits.url
The history files are stored in the following locations:
Windows (Vista and 7/8): C:\Users\\AppData\Local\Google\Chrome\
Windows XP: C:\Documents and Settings\\Local Settings\Application Data\Google\Chrome\
Linux: /home/$USER/.config/google-chrome/ or sometimes
/home/$USER/.config/chromium/
Mac OSX: /Users//Library/Caches/Google/Chrome/Default/Cache
/Users//Library/Application Support/Google/Chrome/Default/
Since the database tables are quite similar the f3e tool has an option of retrieving the user internet browsing information. The other tool that can be used for retrieving browsing information is ChromeAnalysis .
IV. Safari:
Safari too uses SQLite database to store its browsing related data. The files of interest in Safari are Bookmarks.plist, TopSites.plist, History.plist, LastSession.plist, Cookies.plist and Cache.db[55][56].
Bookmarks.plist: This file is mainly used to store bookmarks used by end on Safari .
TopSites.plist: This file stores all the most frequently visit website of the user.
LastSession.plist: This is used to track sites that are currently open by the end user and has active connections to the site. This would also include multiple tabs or multiple windows open to different sites. In cases where the browser would crash unexpectedly, this file is used to restore the previous browsing session.
History.plist: This list contains the date and time when a site was visited and number of times the site was visited.
Cookies.plist: This is similar to History.plist contains the date and time when a site was visited, but additionally also contains account names that were used on the website.
Cookies.db: This too is similar to History.plist contains the date and time when the site was visited but also pictures and other temporary browsing data. This can be extracted using any carving tool to extract the required information.
Typical locations for the browsing data are as per listed below:
Windows (Vista and 7/8):
C:\Users\\AppData\Roaming\Apple Computer\Safari
C:\Users\\AppData\Local\Apple Computer\Safari
Windows XP:
C:\Documents and Settings\\Local Settings\Application Data\Apple Computer\Safari\
C:\Documents and Settings\\Application Data\Apple Computer\Safari\
Mac OSX:
/Users//Library/Safari/
/Users//Library/Caches/com.apple.Safari/

